Automotive Cybersecurity
is Different than Enterprise Cybersecurity
Safety Above All
A car's architecture may resemble a datacenter's architecture. However, the biggest cyber security risk for an enterprise data center is loss of data, while the biggest risk for a car is loss of life.
This is why preventing attacks before they can do any harm is so important for automotive cybersecurity solutions - it’s the only way to assure the ongoing safety of the vehicle.
False Positives Can Kill
Typical enterprise cybersecurity solutions rely on heuristics to try to identify anomalous behavior that indicates an attack.
These heuristic algorithms can generate a lot of false positives, as infrequent, legitimate operations trigger alarms. A false positive in an enterprise can be a distraction and time waster, but in a car, it can endanger the car’s safety.
Blocking a legitimate command that looks like an anomaly can block airbags from deploying or brakes from engaging and result in a fatal car crash.
Updates Can Be Too Late
When a new attack is detected by heuristic cybersecurity solutions, car OEMs and Tier-1 suppliers need time to identify the security vulnerability that was exploited and then develop, test, QA and distribute a security patch to fix it, via an Over the Air (OTA) update.
The OTA update itself may be swift, but the vulnerability identification and remediation typically takes weeks. During that time, cars could find themselves under attack, by hackers exploiting the vulnerability, with disastrous consequences, including loss of life.
Automotive Security Has to be Different
Because the stakes are so high for consumers, car OEMs and Tier-1 suppliers, automotive cybersecurity has to get it right. There’s no room for error, no time for mistakes.

Protect What Matters
Automotive cyberattacks use one of two vectors to infiltrate vehicles:
1. Compromising one of the externally connected electronic control units (ECUs), which serve as gates into the car.
2. Physically hacking the car’s network to impersonate and send commands to safety ECUs from an unauthorized source.
Karamba Enables End-to-End Automotive Security
Karamba developed award winning, patented runtime integrity technology that shuts down both automotive attack vectors – ECUs and in-car networks – to enable end-to-end prevention of automotive cyberattacks. A functional and safe approach of Control Flow Integrity (CFI) is crucial to enable the vehicles' safe functionality without false positives during runtime. For many years the value of CFI was sought after but not possible in the resource-constrained embedded systems. Uniquely enabling this security protection is at the heart of the Karamba innovative patented technology. Karamba’s autonomous security accounts for the uniqueness of a car’s architecture and the automotive industry’s constraints to deliver in-vehicle security. A vehicle’s ECUs are not like a datacenter’s servers or laptops – they must not be changed by a user, only by the OEM – so Karamba focuses on keeping the ECUs running exactly as they are supposed to, according to factory settings, making them impenetrable to attack.
Karamba seamlessly takes an ECU’s factory settings and automatically generates a policy that will instantly detect foreign code and in-memory attacks, and autonomously shut down any exploits, at runtime, with no intervention needed. Karamba also leverages Authentication Encryption in-car networks to prevent hackers from sending malicious commands from unauthorized sources to a vehicle’s safety systems, stopping an attack, immediately, with no overhead.
How Does Karamba’s Autonomous Security Work?
Karamba’s autonomous security is contained in the ECUs’ firmware. It doesn't need constant updates to stay current or rely on heuristic analysis that is prone to false alarms to try to detect an attack. Karamba makes sure that a vehicle’s ECUs run according to factory settings and communicate only with legitimate pre-authorized peer systems. Anything that deviates from the factory settings is blocked or ignored.
To make this autonomous automotive security possible, Karamba brought four major technological breakthroughs to market, including the ability to:
- 1. Automatically lock down an ECU according to its factory settings, identifying and mapping all legitimate binaries and valid function calls.
- 2. Check all operations in runtime and immediately block dropper and in-memory attacks, since they don't comply with factory settings.
- 3. Authenticate all network connections, with zero network overhead.
- 4. Embed itself within the ECU, so it can operate with negligible performance impact.
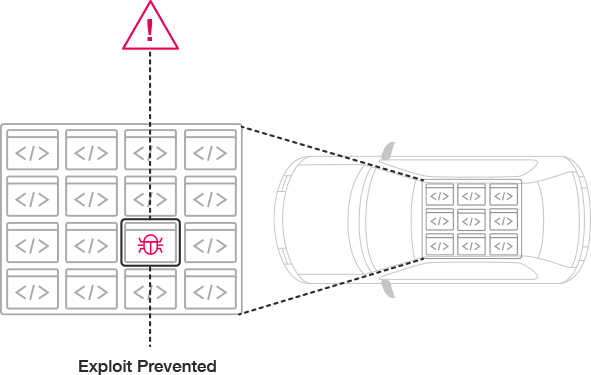
Autonomous Security Benefits

Electronic Control Unit
(ECU) protects itself
The security policy is automatically embedded into the ECU code. Detection and prevention decisions are made locally on the ECU. No connectivity required.

Zero false
positives
Patented deterministic algorithms ensure that only legitimate binaries and function calls, based on factory settings, are allowed to run on the car’s ECU. Everything else is blocked. Period.

Negligible
performance impact
The embedded security policy performs real-time inspection of the operations running in the ECU, with minimal CPU and storage footprints that don't require any hardware change.

Supports
all ECUs
ARM and Intel processors, Linux, QNX, and AUTOSAR operating systems and schedulers are supported. Any controller can be protected.

No anti-malware
updates required
Security policy is based on factory settings. No need to update the policy with new, anti-malware signatures.

No developer
intervention
Patented algorithm automatically generates the security policy, and is embedded automatically into the ECU software. Developers can focus on developing new features instead of spending resources, flushing out hidden security bugs.
Extending ECUs’ Autonomous Security into the Car’s Networks
In addition to protecting the ECUs themselves, Karamba can protect the communications to the ECUs. This ensures that safety ECUs, such as brakes and air bags, receive commands only from authorized sources, so they operate as they should.
Karamba’s autonomous network hardening security software uses patented runtime integrity technology to automatically authenticate all network communications. This prevents attackers from physically hacking into the car or impersonating a legitimate source and sending malicious commands to the car’s ECUs that can risk the car’s safety.
The authentication is done without requiring the ECUs’ Tier-1 providers to change their development methods or change the ECU’s architecture. By automatic encryption of the ECUs’ traffic with zero network overhead, car networks can be authenticated, so malicious commands sent from non-authorized sources are automatically ignored and prevented from doing any harm.
Want to learn more?
Contact UsIsrael
24 HaNagar Street
Hod Hasharon
45277-13
Tel: +972 9 88 66 113
USA
41000 Woodward Ave
Building East, Suite 350
Bloomfield Hills, MI 48304
Tel: +1 833 4KARAMBA