The anonymity of the Darknet has attracted criminals, including cybercriminals and threat actors who offer attack services, research and development of vulnerabilities of websites and recently - more and more IoT devices.
The Darknet is an overlay network, which operates on the standard Internet infrastructure, and allows access to content almost completely anonymously, using dedicated software or a unique setting.
Unlike the “regular” browser we use, such as Google Chrome or Firefox, to access Darknet it is necessary to download a special browser called “TOR” (The Onion Router), which will provide almost complete anonymity to the end-user.
 Figure 1 - TOR project website
Figure 1 - TOR project website
Like anything in Darknet, the URL of Darknet websites will look different and complicated; In fact, it is impossible to buy or create a simple URL, like google.com. The URL will be a combination of random letters and numbers, and instead of the standard URL extensions, such as “.com”, “.net”, “.io”, etc., there will be the “.onion” extension.
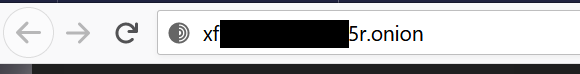 Figure 2 - Sample Darknet URL
Figure 2 - Sample Darknet URL
The unique URL extension of the websites in Darknet blocks index engines like Google and Bing from indexing the sites in Darknet. In fact, to enter a specific website in Darknet, it is necessary to know its URL and only then enter it.
The almost complete anonymity allows freedom fighters and human rights activists to report on what is happening in their countries – for example, the state of civil war in Syria or the complicated situation in Iran – which would put them in jail if they used the “regular internet”.
But the anonymity has also attracted criminals to use the Darknet, and to sell services and products through this network. Some of the services and products that can be bought in the Darknet are:
- Fake money
- Stolen goods
- Fake ID
- Drugs
- Guns, and more
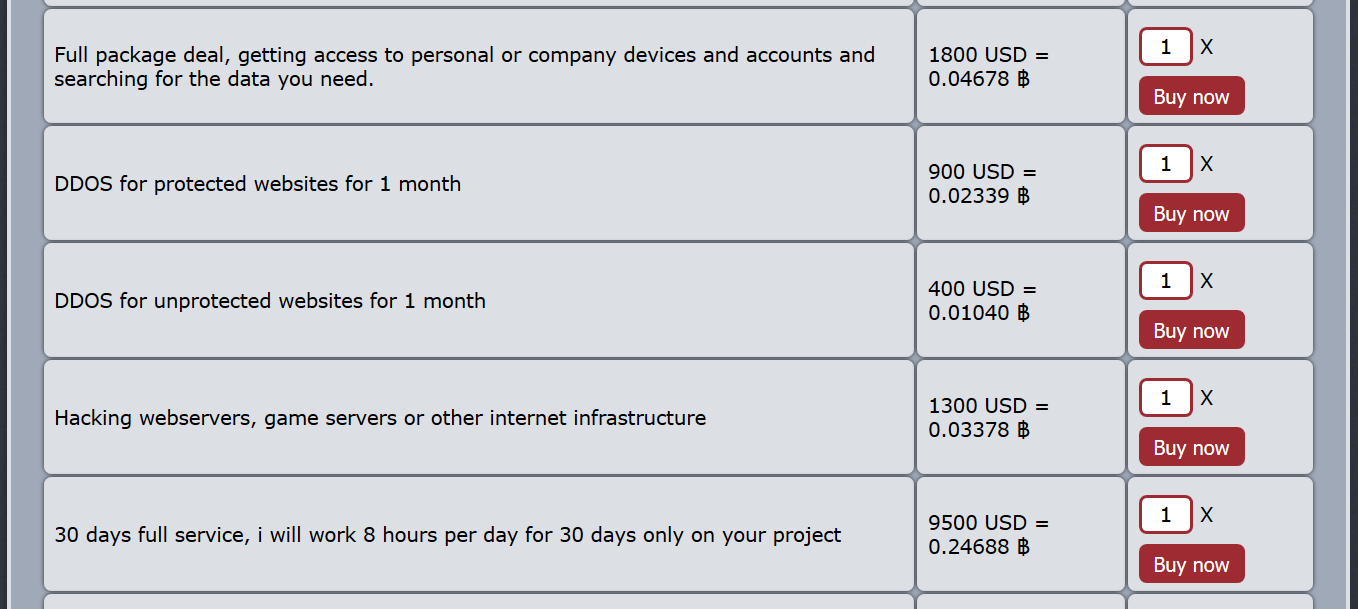 Figure 3 - Darknet website offering DDoS-as-a-Service
Figure 3 - Darknet website offering DDoS-as-a-Service
But it does not end there. The Darknet should bother legitimate businesses as well, because in addition to “ordinary” criminals, cybercriminals and threat actors have also “discovered” the Darknet, operating there and offering attack services, research, and development vulnerabilities for websites, dedicated platforms, IoT devices and more.
The most prominent platforms on which 1-day (or n-day) vulnerabilities can be found are operating systems such as Windows, Linux, and Android; Internet browsers like Internet Explorer, Google Chrome, and Mozilla Firefox; and applications such as Flash player, PDF reader, and more.
In the era of IoT, when operating systems and browsers are connected to physical devices such as critical infrastructures and vehicles, it gets even worse. Recently, our security research team at Karamba Security has detected an attack group that exploited a known critical vulnerability and sells the exploit code that allows a remote attacker to get complete control over a common vehicle model (Remote Code Execution or RCE). Detecting this kind of exploit help prioritize vulnerability fixing and give some vulnerabilities priority over others.
This is just one example of how 1-day vulnerabilities may be exploited, and the exploits sold to threat actors. The way for manufacturers to address such exploits is by embedding deterministic protection into the device. Such protection will prevent the RCE exploits, without relying on patching that may take time, or that in certain cases may not even be possible.
Contact Karamba Security to protect your IoT devices.
