We are sharing our customers’ aggregated experience of the most risky components in connected EVs.
Karamba Security is at the forefront of Cybersecurity assessment and mitigation for Electric Vehicles. We are sharing our customers’ aggregated experience of the most risky components in connected EVs. This data correlates directly to the items that required most attention while preparing for UN ECE R155 and ISO21434 submissions.
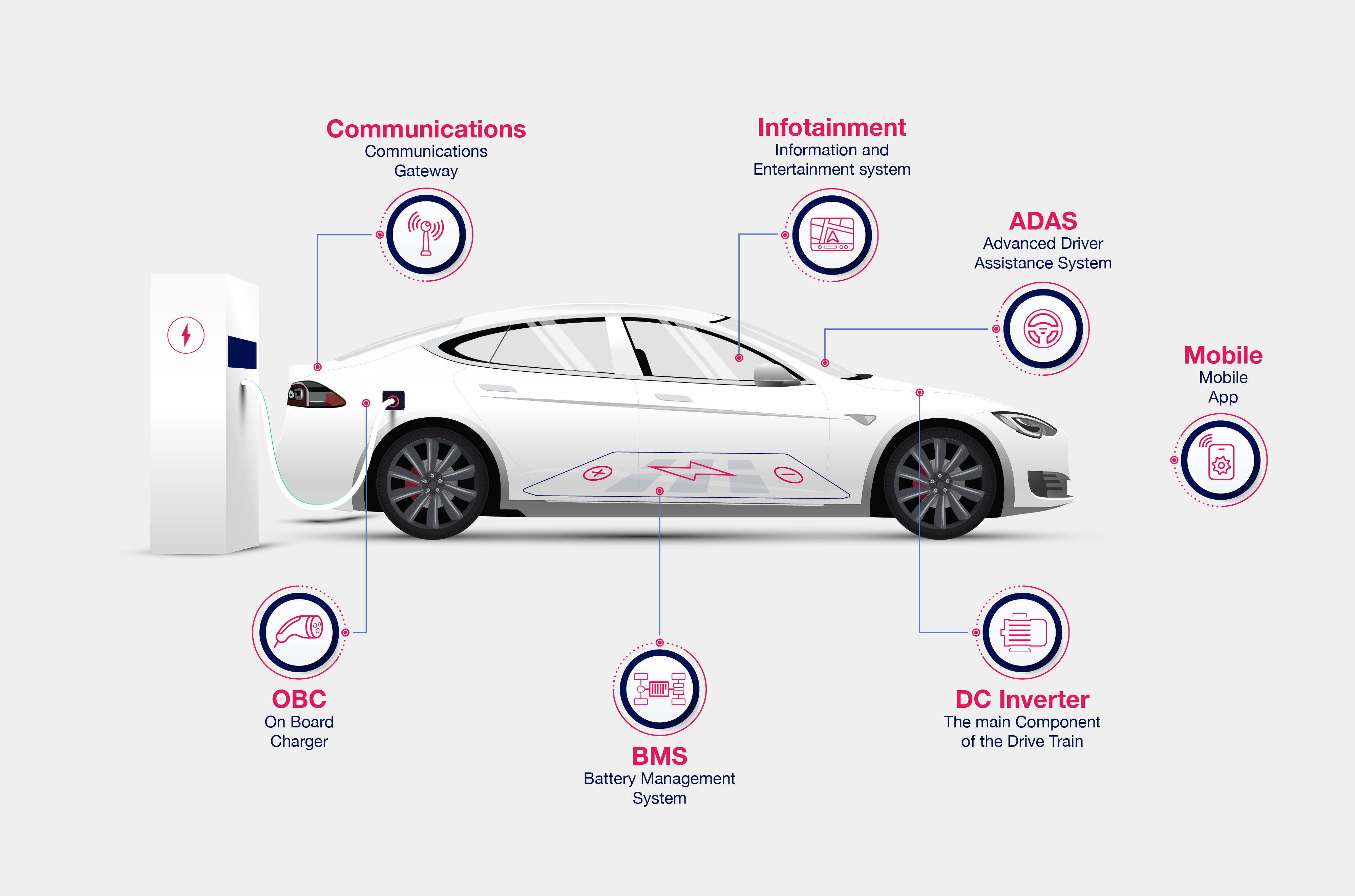 Connected EV Components
Connected EV Components
OBC (On Board Charger) – The On-Board Chargers manage the charge of the car from AC sources, and in the future will also provide power back to the grid. Risks for OBC are around charging with higher currents than it is safe, having access open enabling access to other ECUs and leakage of sensitive IP or customer data
BMS (Battery Management System) – Many new EV manage High Voltage DC charging directly through the BMS, making the BMS susceptible to the same risks as the OBC. Additionally, the BMS may create driving hazards by falsely reporting the battery to be depleted, or cutting power to the motors and halting the car in mid highway.
Infotainment – The Infotainment system has rich functionality and lots of processing power. It often also allows control of windows/doors and even remote start of the car. Risks are: remote control of this unit allowing breaking into the car and stealing it, distracting the driver while driving, and in some car implementations we’ve seen even vulnerabilities reaching safety related tasks like acceleration and braking.
Communications Hub/Gateway – The communications hub is used in some cars to separate outward facing communications from the rest of the car, and thus segment the risk. This makes those units an easy and preferred attack vector, extending any other attack vectors that were initially blocked by a gateway.
ADAS (Autonomous Driving and Assisted Driving) – Having fully autonomous or even L3 assisted driving means that a wrong guidance from the system due to erroneous sensor input or wrong decisions can cause catastrophic results. The ADAS vulnerabilities focus on two scenarios above others: Replacement of firmware, and Validation of sensor input.
DC Inverter – This is the main component of the drive train. Unauthorized access to the inverter functions can result in safety-critical risks including the loss of life.
Owner Mobile Application – The security of this application’s storage of personal data, as well as the security of the APIs used by the application, may not have safety impact, but they affect one of the most painful problems for the owner: theft using impersonation, replication and/or replay methods.
It is critical that each of the above vehicle elements be reviewed thoroughly as part of the EV TARA. Vulnerabilities and possible attack impacts must be taken into consideration when prioritizing action items and creating a mitigation plan.
Review our Products and Services to see how they can help you comply with cybersecurity regulations.
Contact us to learn how ISO21434 affects the EV ecosystem.
